Table of Contents
- The Password Problem: Why We Need Better Solutions
- Understanding Biometric Authentication Types
- The Security Advantage: More Than Convenience
- Designing Biometric Authentication: UX Best Practices
- Implementation Considerations for Designers
- Measuring Success: Biometric Authentication Metrics
- The Future of Biometric Authentication
- Conclusion: Balancing Security and Simplicity
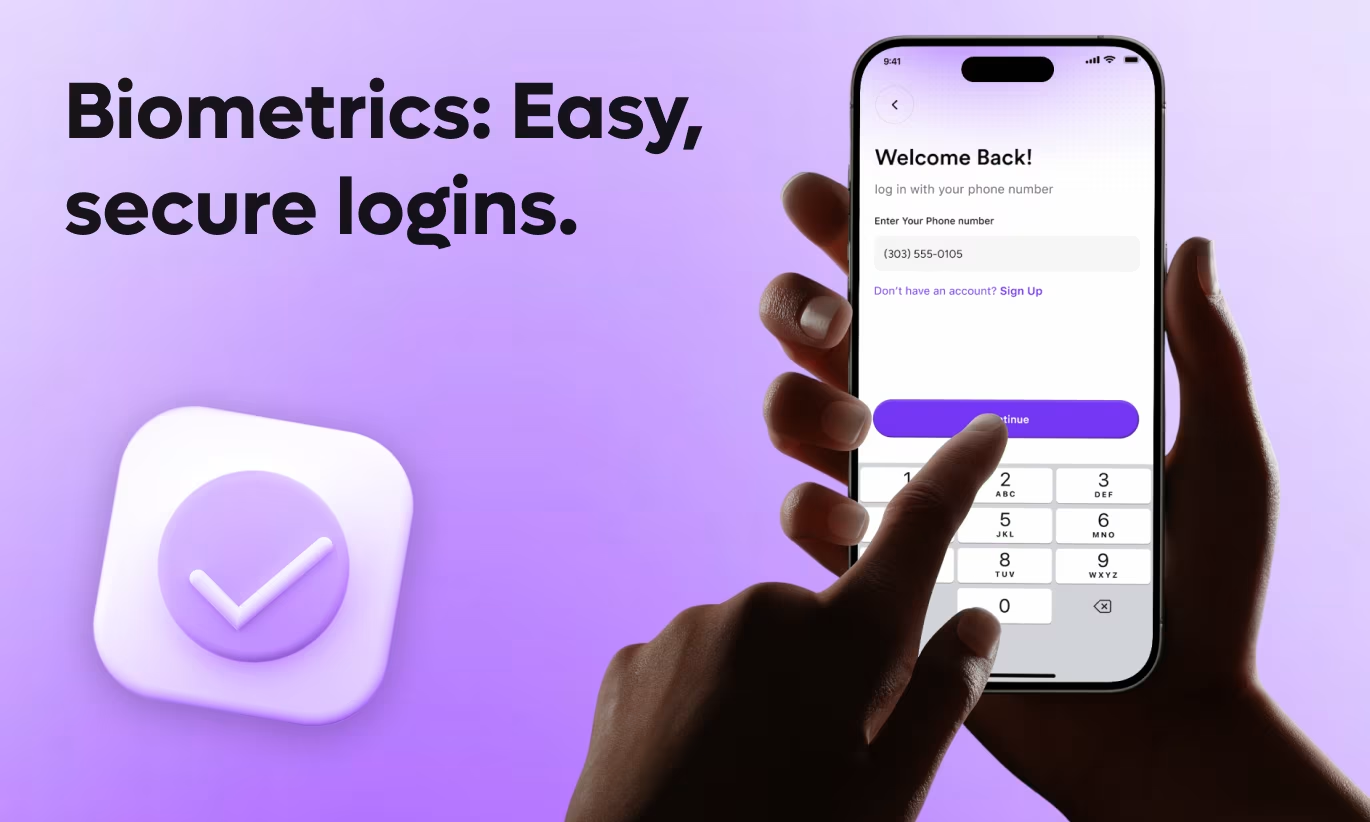
In an era where the average person manages passwords for dozens of apps and services, login friction has become a major user experience challenge. Enter biometric authentication - a technology that's transforming how users access their applications while simultaneously enhancing security.
From fingerprint scanners to facial recognition, biometric authentication is no longer a luxury feature reserved for banking apps; it's rapidly becoming an expected standard across all mobile applications.
The Password Problem: Why We Need Better Solutions
Traditional password-based authentication creates significant friction in the user experience. Studies show that 78% of users have forgotten a password in the past 90 days, and the average user resets their password 7-10 times per year. This friction leads to abandoned sessions, decreased engagement, and frustrated users.
Beyond inconvenience, passwords present serious security vulnerabilities. Despite countless warnings, users continue to reuse passwords across multiple services, choose weak combinations, and fall victim to phishing attacks. The 2023 Verizon Data Breach Investigations Report found that 81% of hacking-related breaches leveraged stolen or weak passwords.
Biometric authentication addresses both problems simultaneously. It eliminates the need to remember complex passwords while providing stronger security through unique biological characteristics that can't be easily replicated or stolen.
Understanding Biometric Authentication Types
Fingerprint Recognition
Fingerprint authentication has become the most widely adopted biometric method, with over 60% of smartphones now equipped with fingerprint sensors. The technology maps unique ridge patterns on fingertips, creating a mathematical representation that's stored securely on the device.
Advantages:
- Highly accurate (less than 1 in 50,000 false acceptance rate)
- Fast authentication (typically under 1 second)
- User familiarity and acceptance
- Works offline without internet connectivity
- Low implementation cost
Considerations:
- Can be affected by wet or dirty fingers
- Requires physical touch (hygiene concerns in shared devices)
- Not suitable for users with certain skin conditions
- Sensor placement impacts usability
Facial Recognition
Face ID and similar facial recognition technologies analyze over 30,000 points on a user's face to create a detailed depth map. Modern systems use infrared cameras and neural networks to ensure accuracy even in varying lighting conditions.
Advantages:
- Completely touchless experience
- Works from natural viewing distance
- Harder to spoof than fingerprints
- Harder to spoof than fingerprints
- Adapts to appearance changes (glasses, hairstyle)
- Intuitive and effortless for users
Considerations:
- Requires front-facing camera hardware
- Privacy concerns about facial data storage
- May struggle with identical twins
- Less effective with masks (though improving)
- Lighting conditions can affect accuracy
Voice Recognition
Voice biometrics analyze unique vocal characteristics including pitch, tone, cadence, and speech patterns. While less common in app authentication, voice recognition excels in hands-free scenarios.
Advantages:
- Ideal for accessibility
- Works without screen interaction
- Natural for voice-first applications
- Can authenticate during normal conversation
- Useful for phone-based services
Considerations:
- Background noise interference
- Voice changes due to illness
- Recording and spoofing concerns
- Requires audio permissions
- Less user acceptance for general apps
Iris and Retinal Scanning
These advanced methods scan unique patterns in the eye's iris or retina. While highly secure, they're less common in consumer applications due to hardware requirements and user comfort concerns.
The Security Advantage: More Than Convenience
Biometric authentication doesn't just improve user experience—it significantly enhances security. Unlike passwords, biometric data is:
Unique to Each Individual: No two fingerprints or facial structures are identical, making impersonation extremely difficult.
Non-transferable: You can't share your fingerprint the way you might share a password with a family member or colleague.
Difficult to Replicate: While not impossible, creating fake biometric credentials requires sophisticated technology and access to the original biometric sample.
Impossible to Forget: Your biological characteristics are always with you, eliminating the "forgot password" problem entirely.
Modern biometric systems also implement "liveness detection" to prevent spoofing attempts using photos, videos, or fake fingerprints. These security layers analyze subtle movements, temperature, and other characteristics that prove the biometric sample comes from a living person.
Designing Biometric Authentication: UX Best Practices
1. Make It Optional, But Encouraged
Never force users to enable biometric authentication. Some users have privacy concerns, while others may have accessibility challenges or devices without biometric hardware.
Best practice: Present biometric setup as an opt-in feature during onboarding with clear benefits explained. Use language like "Login in seconds with your fingerprint" rather than technical jargon.
Fallback strategy: Always provide alternative authentication methods (password, PIN, or email verification) so users can access their accounts even when biometrics fail or aren't available.
2. Provide Clear, Immediate Feedback
When users attempt biometric authentication, they need instant feedback about what's happening.
Success states: Use haptic feedback, visual checkmarks, and brief confirmations. The authentication should feel instantaneous—aim for under 1 second from biometric scan to authenticated state.
Failure states: When authentication fails, provide specific, helpful guidance:
- "Fingerprint not recognized. Try again or use your password."
- "Face not detected. Position your face within the frame."
- "Too many attempts. Please use your password."
Loading states: For systems requiring server verification, show clear progress indicators so users understand processing is occurring.
3. Implement Progressive Disclosure
Don't overwhelm users with all biometric options immediately. Introduce features contextually when they're most relevant.
Example flow:
- User completes initial registration with password
- After first successful login, prompt: "Save time on your next login with Face ID?"
- If declined, remind them in settings that the option exists
- For repeated manual logins, gently resurface the biometric option
4. Design for Authentication Failure
Biometric systems aren't perfect. Sensors fail, conditions change, and false rejections occur. Your design must gracefully handle failures without frustrating users.
Failure recovery:
- Limit retry attempts (typically 3-5) before requiring fallback authentication
- Don't immediately lock accounts after biometric failures
- Explain why failure might have occurred with actionable suggestions
- Make fallback methods easily accessible without buried navigation
5. Consider Security Context
Not all actions require the same security level. Design your authentication flow to match the risk profile of different actions.
Low-risk actions: Viewing account information, browsing content Authentication: Biometric or session persistence
Medium-risk actions: Making purchases, updating profiles Authentication: Recent biometric verification (within last 5-15 minutes)
High-risk actions: Transferring money, changing security settings Authentication: Fresh biometric verification plus additional factor (password, OTP)
This tiered approach balances security with usability, avoiding authentication fatigue from constantly re-verifying identity.
6. Respect User Privacy
Biometric data is highly personal. Users need assurance that their biological information is protected.
Privacy principles:
- Store biometric data locally on-device when possible, not on servers
- Use encrypted secure enclaves (like iOS Secure Enclave or Android Keystore)
- Never transmit raw biometric data over networks
- Provide clear privacy policies explaining data handling
- Allow users to delete biometric data easily
- Be transparent about what happens to biometric information if account is deleted
Trust-building communication: "Your fingerprint data is encrypted and stored only on your device. We never see or store your actual fingerprint."
7. Accommodate Edge Cases and Accessibility
Design for users who can't use biometric authentication due to physical limitations, device constraints, or personal preferences.
Accessibility considerations:
- Ensure keyboard navigation for all authentication flows
- Provide screen reader compatibility with clear announcements
- Offer alternative authentication for users with disabilities
- Don't rely solely on color to indicate success/failure
- Support voice commands for hands-free authentication where appropriate
8. Design Seamless Onboarding
The first biometric setup experience sets user expectations and adoption rates.
Onboarding best practices:
- Explain benefits clearly: "Login 5x faster with your fingerprint"
- Show visual demonstrations of how to use the feature
- Handle setup failures gracefully with retry options
- Allow skipping during initial setup with easy re-activation later
- Confirm successful setup with a test authentication
- Remind users that fallback methods remain available
Implementation Considerations for Designers
Platform-Specific Patterns
iOS (Face ID & Touch ID):
- Follow Apple's Human Interface Guidelines
- Use system authentication dialogs when possible
- Implement fallback to device passcode seamlessly
- Request biometric permissions with clear justification
- Handle authentication cancellation gracefully
Android (Fingerprint & Face Unlock):
- Support BiometricPrompt API for consistency
- Account for device fragmentation (different sensor types/locations)
- Provide clear fallback to pattern/PIN/password
- Test across multiple device manufacturers
- Consider both in-screen and back-mounted fingerprint sensors
Performance Optimization
Biometric authentication should feel instantaneous. Optimize your implementation:
- Pre-load authentication UI components
- Minimize network calls during authentication flow
- Cache session tokens appropriately after successful authentication
- Use progressive loading for post-authentication content
- Implement offline authentication capabilities when possible
Error Prevention
Design proactively to prevent authentication failures:
- Provide visual guidance for proper finger placement
- Show facial recognition framing guides
- Warn users about environmental factors (lighting, gloves)
- Educate users during setup about optimal conditions
- Allow biometric recalibration if frequent failures occur
Measuring Success: Biometric Authentication Metrics
Track these KPIs to evaluate your biometric authentication implementation:
Adoption Rate: Percentage of eligible users who enable biometric authentication Target: 60-80% adoption within 30 days of account creation
Success Rate: Percentage of authentication attempts that succeed on first try Target: 95%+ first-attempt success rate
Time to Authenticate: Duration from authentication prompt to verified state Target: Under 1 second average
Fallback Usage: How often users resort to password/PIN instead of biometrics Target: Less than 5% of authentication attempts
Support Tickets: Reduction in password-related support requests Target: 40-60% reduction after biometric implementation
The Future of Biometric Authentication
Biometric technology continues evolving rapidly. Emerging trends include:
Behavioral Biometrics: Authentication based on typing patterns, walking gait, and interaction behaviors that happen passively without explicit user action.
Multi-Modal Biometrics: Combining multiple biometric factors (face + voice, fingerprint + iris) for enhanced security in high-stakes applications.
Continuous Authentication: Rather than one-time login, continuously verifying identity through behavioral patterns throughout the session.
Ambient Authentication: Using contextual factors (location, device, network, time patterns) combined with lightweight biometrics for frictionless yet secure access.
Conclusion: Balancing Security and Simplicity
Biometric authentication represents a significant leap forward in solving the tension between security and usability. When designed thoughtfully, it eliminates password friction while providing stronger security than traditional methods.
The key to successful implementation lies in understanding that biometric authentication isn't just a technical feature—it's a user experience that must be designed with the same care and attention as any other aspect of your application. Focus on clarity, provide appropriate fallbacks, respect user privacy, and continuously optimize based on real-world usage data.
As users increasingly expect seamless, secure experiences, biometric authentication has moved from competitive advantage to baseline expectation. Applications that implement it well will benefit from higher engagement, improved security, and users who appreciate the effortless experience.
At Orbix Studio, we specialize in designing secure, user-friendly authentication experiences that balance cutting-edge technology with intuitive design. Whether you're implementing biometric authentication for the first time or optimizing an existing system, we bring strategic UX thinking and technical expertise to create login experiences that users love.
Ready to simplify authentication in your app? Let's design a biometric experience that delights users while enhancing security.
Fresh UI/UX Ideas, Straight to Your Inbox